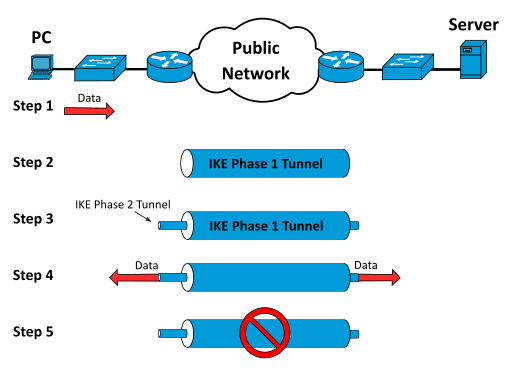
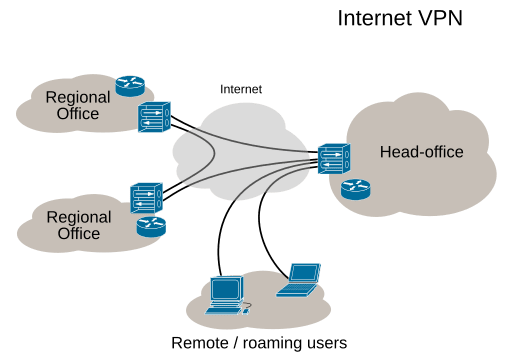
Introduction – Definition & information about VPNs

A VPN stands for Virtual Private Network and is a means of connecting through a network over a secure encrypted connection to secure all data in transit. These day’s VPN platforms are available in the hundreds such as the best VPNs for Australia and can be used for a variety of different purposes such as bypassing GEO content restrictions, accessing P2P services like BitTorrent or just protecting your data if your traveling and using an unfamiliar network.
This powerful technology scrambles your information, masks your IP address, and hides your physical location, making it impossible for third parties to track your online behavior. Instead of traveling along the open internet highway, your data moves through a secure, private pathway that keeps your digital life protected.
Some VPN platforms to consider:
How Does a VPN Work?
Whether you’re working remotely, accessing region-restricted content, or simply browsing, a VPN provides the privacy and security essential for a safer online experience. With increasing concerns about data privacy, understanding what a VPN is and how it works has never been more important. When you connect to a VPN application/server you effectively tunnel all your network traffic through another server through a secure connection which then makes requests and or retrieves data on your behalf utilising Cryptography.
VPN applications can help to preserve your privacy by hiding your IP address on the network your connected to and access websites that may be blocked in your country or region.
These networks often have weak passwords and are vulnerable to traffic analysis attacks whereby a malicious user can intercept all traffic and potentially capture emails, messages, images and or voice & video data such as video calls.
VPN Tunnels and Encryption
VPN tunnels and encryption safeguard user data by creating a secure pathway between devices and the internet. Encryption protocols like IPSec, OpenVPN, and L2TP scramble data into indecipherable code before transmission. In real time, data moves through the tunnel, remaining unreadable to unauthorized parties such as hackers or ISPs. When data arrives at the VPN server, it’s decrypted and sent to its final destination, keeping the content invisible to others during transit.
VPN Servers and IP Address Masking
VPN servers and IP address masking enable users to appear as if browsing from different locations. When connected, a user’s internet traffic shows the server’s IP address instead of their own. Server options span multiple countries, allowing for access to geo-restricted resources and enhanced online privacy. Online activities, original IP addresses, and physical locations stay hidden from websites, ISPs, and trackers, leveraging VPN server infrastructure for anonymous browsing.
Uses for a VPN
VPN technologies have multiple use-cases this section explains some examples of common uses and how VPN applications work in the relevant context:
Secure Remote Access
Virtual private networks have a number of different uses, their most common use is by organizations who have large teams or operate in multiple locations. A VPN in this case would facilitate the sharing of files between people from different locations that may potentially be insecure or not abide by company standards for network security.
Cryptocurrency
![]()
Some users also connect to VPNs they trust when logging into social media accounts on unfamiliar networks, online payment platforms as well as Cryptocurrency exchanges from different countries such as Australia, New Zealand, Dubai or Norway.
Streaming
![]()
Another use of these networks is to circumvent content blocking systems which may restrict access to content based on the country of the user. For example a video may only be available in the United Kingdom and not available to users located in Poland.
In this example a VPN server located in the UK could be used to access the content for the user in another country. In other circumstances some streaming services like Netflix, Amazon Prime and others will only showcase some content in some regions whilst delaying releases in other areas, a VPN with a different country IP can get around this and access local content within streaming platforms.
Common Protocols
Most VPN technologies will utilize different network protocols, here are the most common ones associated with the technology.
- IPSec: This is a set of protocols formulated by the IETF to facilitate the secure exchange of packets on the IP layer, IPSec has two encryption modes which are the transport and tunnel.
- PPTP: The Point-to-Point Tunneling protocol was made in order to create VPN’s by Microsoft and other technology vendors collectively known as the PPTP forum.
- L2TP: This stands for Layer 2 Tunneling protocol, it is an extension of the PPP protocol that allows internet service providers such as Telstra to operate VPN servers.
Potential advantages

The biggest advantage of using a VPN is the fact you can establish secure connections when traveling and unsure of the security of your current network. They can also help by adding a level of privacy by safeguarding your network traffic from malicious adversaries on the network or from websites actively tracking your movements around the web.
Potential disadvantages & The dangers of using free VPN’s

The major disadvantage of using a VPN is that you are trusting the server to safeguard your information, just because your connection to the server is encrypted doesn’t mean the provider isn’t logging data or worse engaging in data mining with your sensitive information.
This concern is mostly an issue with consumer VPN apps particularly “free vpns” for both desktop and mobile devices which will often weaken security more then they claim to improve and may even perform other nasty actions like inject malware or ads into pages you visit.
In order to overcome this problem you can use various open source software such as OpenVPN which allows one to set-up his/her own server which can be configured to connect from desktop and mobile devices. Other disadvantages of using this technology is that depending on where the server is located your internet connection may be much slower as the data will need to be encrypted first which can slow down load times for websites and applications.
Differences between an Access VPN & VPN Tunnel
VPN tunnel
A tunnel is the most common form of VPN server commonly called a “Privacy VPN” as it will direct the entire network traffic of a device through a remote server. All requests are then funneled through the server and made on behalf of the client. Tunnels are most commonly used by consumers
Access VPN
This type of server is set-up purely for the purpose of allowing remote connections (usually to an internal network or locally hosted service), it commonly used by enterprises to allow employees to remotely access the corporate network securely so they can access their files.
A system like this won’t protect all network traffic but only aid in establishing a secure encrypted connection to the network or server configured by the organization.
Other Types of VPNs
Site-to-Site VPN
Site-to-site VPNs securely connect multiple office networks, allowing seamless communication across geographically distant locations. Organizations with branch offices use site-to-site VPNs to establish a unified, private network for resource sharing and secure internal communication. These VPNs often use IPsec as the primary protocol and rely on gateway-to-gateway or router-to-router connections to ensure encrypted data transmission between sites.
Personal and Mobile VPN
Personal VPNs encrypt internet traffic on individual devices, providing enhanced privacy, hiding users’ IP addresses, and bypassing content restrictions. People use personal VPNs to access blocked content and prevent online tracking. Mobile VPNs are designed for smartphones and tablets, maintaining stable, encrypted connections even when users switch between Wi-Fi and cellular networks. This ensures uninterrupted data protection and secure browsing on the go.
| VPN Type | Typical Protocols | Architecture | Main Use Case |
|---|---|---|---|
| Remote Access VPN | SSL/TLS | Client-server | Secure remote access for individual users |
| Site-to-Site VPN | IPsec | Gateway-to-gateway | Secure connectivity between branch offices or company sites |
| Personal VPN | OpenVPN, WireGuard | Client-server | Private, secure browsing and geo-unblocking |
| Mobile VPN | Various | Client-server/App | Secure mobile data across changing networks |
Why Use a VPN?

VPNs increase online privacy and security while enabling access to digital content from anywhere. Encrypting internet traffic and obscuring IP addresses, VPNs address multiple risks and challenges in today’s online environment.
Protecting Privacy and Security
VPNs protect privacy and security by encrypting data in transit and hiding users’ real IP addresses. This encryption prevents ISPs, hackers, advertisers, and government agencies from monitoring browsing activity or intercepting sensitive information. For example, users shield login credentials, payment details, and personal communications from interception on any network.
Accessing Restricted Content
VPNs enable access to restricted content by routing traffic through servers in various locations. By masking the true geographic source of a connection, VPNs let users access streaming services, websites, and digital platforms that are unavailable in certain countries. For instance, VPNs allow viewing of shows exclusive to another region on platforms like Netflix.
Securing Public Wi-Fi Connections
VPNs secure public Wi-Fi connections by creating an encrypted tunnel for all data exchanged over open hotspots. Cybercriminals often exploit unprotected networks in airports, cafes, and hotels to steal data, but VPN encryption blocks unauthorized parties from reading captured traffic. Users can access personal and financial accounts over public Wi-Fi with increased safety.
Bypassing Censorship and Tracking
VPNs bypass censorship and tracking by disguising internet traffic and making online actions less detectable. This capability helps users overcome government-imposed internet blocks, workplace or school filters, and location-based restrictions. VPNs also limit third-party tracking by advertisers and minimize ISP throttling based on detected activity, resulting in freer and more equitable internet access.
Key Features to Look for in a VPN
Selecting an effective VPN depends on critical features that impact privacy, security, and access. Reliable VPNs provide industry-standard encryption, maintain user anonymity, offer a broad server network, and ensure persistent protection through advanced tools.
Encryption Protocols
Encryption protocols safeguard VPN data during transmission. Top protocols include OpenVPN, which uses 256-bit AES encryption and supports both TCP and UDP for robust security; WireGuard, known for rapid connections and ChaCha20 encryption; and IKEv2/IPSec, balancing speed and protection for mobile browsing. Each protocol delivers distinct security levels for various devices and use cases.
| Protocol | Encryption | Routing | Use Case |
|---|---|---|---|
| OpenVPN | 256-bit AES | TCP/UDP, SSL/TLS | Versatile, secure connections |
| WireGuard | ChaCha20 / AES-256 | UDP | Fast, modern deployments |
| IKEv2/IPSec | 256-bit AES | UDP | Mobile, stable connections |
No-Logs Policy
A no-logs policy prevents providers from storing user activities or connection metadata. Rigorous no-logs standards increase user privacy by ensuring browsing history, IP addresses, and session data remain unrecorded. Leading services disclose their policies clearly and verify claims through independent audits. A strong no-logs environment protects against data exposure risks even under external legal requests.
Server Locations
Extensive server locations improve access and performance. VPNs operating networks in 50–100 countries reduce latency and enable users to bypass georestrictions, supporting streaming and region-specific content access. Greater server diversity helps locate nearby servers, increases speeds, and expands options for privacy-sensitive routing.
Kill Switch and Additional Security Tools
A kill switch halts internet traffic if the VPN connection drops, preventing accidental data leaks. Additional tools like DNS leak protection, malware blockers, and multi-hop routing further shield user data from exposure. Incorporating these security layers ensures confidentiality remains intact even during connection interruptions or advanced cyber threats.
Potential Limitations and Considerations
Using a VPN enhances privacy and security but introduces important trade-offs. Certain limitations impact speed and performance while legal and ethical factors vary by jurisdiction and use case.
Speed and Performance
VPN connections often reduce internet speed. Encryption and rerouting through distant servers increase latency and lower bandwidth. For example, OpenVPN typically reaches up to 400 Mbps download with latency between 50-100 ms, while WireGuard can achieve up to 600 Mbps with 20-50 ms latency. Server distance, user load, and time of day can cause further slowdowns, particularly for streaming, gaming, or large downloads. Free or overloaded VPN services may cap data and restrict speeds, with some providers operating in only a small number of global locations. Users may encounter dropped connections, which can interrupt activity and, without a kill switch, cause data leaks. Improper configuration or incompatible operating systems may create vulnerabilities and unpredictable behavior.
| Protocol | Approximate Speed (Download/Upload) | Latency (ms) | Encryption |
|---|---|---|---|
| OpenVPN | Up to 400 Mbps / 100 Mbps | 50-100 | AES-256 |
| WireGuard | Up to 600 Mbps / 150 Mbps | 20-50 | ChaCha20Poly1305 |
| SSTP | Up to 300 Mbps / 50 Mbps | 50-100 | AES-256 |
| IKEv2/IPSec | Up to 500 Mbps / 100 Mbps | 30-70 | AES-256 |
How to Set Up and Use a VPN
Setting up and using a VPN improves online privacy by encrypting internet traffic and masking IP addresses. The process involves selecting a VPN service, installing the software, and connecting devices to servers in the desired location.
Choosing and Installing a VPN Service
Selecting and installing a VPN service ensures secure and reliable protection. Users evaluate VPNs by comparing encryption standards, privacy policies, server locations, and device compatibility. Most reputable VPN services offer AES-256 encryption, maintain no-logs policies, and provide server options in 50 or more countries. Installation typically involves downloading the VPN client for Windows, macOS, Android, or iOS from the provider’s website or official app store. Some services also provide browser extensions for Chrome or Firefox that encrypt only browser data. After installing the app, users log in with their credentials to activate the software.
Connecting Your Devices
Connecting devices to a VPN establishes an encrypted tunnel between user devices and remote servers, securing all data in transit. To connect, users launch the VPN app, select or are automatically assigned a server based on location or purpose (e.g., streaming, privacy), and initiate the connection by clicking the “connect” button. Advanced features like auto-connect, kill switch, or split tunneling may be enabled in the app’s settings for added customization. Users verify connection status in the app dashboard or by checking an IP address lookup site to confirm the VPN server’s location. All internet activity routes through the secure tunnel as long as the VPN remains active.
Key Takeaways
- A VPN (Virtual Private Network) creates an encrypted tunnel between your device and the internet, protecting your data from outside observation
- By scrambling your information and masking your IP address, VPNs prevent third parties from tracking your online activities
- VPNs hide your physical location, allowing you to browse anonymously and access region-restricted content
- Using a VPN is especially valuable for remote work situations where secure connections are essential
- With growing concerns about data privacy, VPNs provide a necessary layer of security for safer everyday browsing
Frequently Asked Questions (FAQs)

What is a VPN?
A VPN, or Virtual Private Network, is a technology that establishes a secure and encrypted connection across a public network, such as the internet, in order to safeguard your online privacy and data.
Why should I use a VPN?
By concealing your IP address, encrypting your internet traffic, and preventing third parties from monitoring your online activities, VPNs can assist to improve your online security and privacy.
Is using a VPN legal?
Using a VPN for lawful purposes is permitted in most countries. It is crucial to emphasize, however, that utilizing a VPN for unlawful purposes remains illegal.
Can I access geo-restricted content with a VPN?
Yes, a VPN can let you access geo-restricted content by making your browser appear to be in a different location.
Are there any dangers with using VPNs?
While VPNs enhance security, they aren’t without risks. Some dangers include malware-infected VPN servers, compromised credentials, potential data leaks from misconfigurations, and untrustworthy VPN providers that might log your activities. Always choose reputable VPN services with strong security practices, clear privacy policies, and a proven track record of protecting user data.
How much does a VPN cost?
VPN pricing varies widely. Free VPNs exist but often have limitations and may sell your data. Paid VPNs typically range from $2-$12 per month, with discounts for longer subscriptions. Premium services offering stronger security, faster speeds, and more server locations generally cost $5-$10 monthly. Many providers offer money-back guarantees, allowing you to test their service risk-free.
Does Chrome have a built-in VPN?
No, Google Chrome doesn’t have a true built-in VPN. Chrome offers a “secure DNS” feature and Google has a “VPN by Google One” service for paid subscribers, but these aren’t integrated directly into the browser. For comprehensive VPN protection, you’ll need to install a third-party VPN service, either as a browser extension or, preferably, as a system-wide application for complete device protection.
Is it worth having a VPN at home?
Yes, a VPN is valuable at home because it protects your privacy from your internet service provider’s monitoring and potential data selling. It secures all your devices on your home network, prevents targeted ads, allows access to geo-restricted content, and adds a layer of security for smart home devices. With increasing online surveillance and data breaches, home VPN use has become a practical privacy measure.
How does a site-to-site VPN differ from a remote access VPN?
A site-to-site VPN connects complete networks, most commonly two or more branch offices or data centers. A remote access VPN, on the other hand, enables remote users to securely connect to a corporate network.
Do VPNs work on all devices and Operating Systems?
Yes most VPN applications work across different Operating Systems such as Windows, macOS, Linux, Android and iOS as well as different models of routers such as TP Link and Netgear.
What features should I look for in a VPN service?
Look for strong encryption, a no-logs policy, a large server network, kill switch, DNS leak protection, and compatibility with your devices. These features help ensure privacy, security, and good performance.
Conclusion
All up these servers can be very useful in safeguarding your data however one should be careful to choose a provider who has a privacy policy which will protect your data and not harm your security.
Be sure to share this if you found it useful, Follow AGR Technology on Twitter & Pinterest for updates or check out other entries on the I.T glossary or our video guides.
Other pages on our glossary & website:
Top VPN Servers & Apps for the Netherlands
VPN Servers/Services for Belgium
DDoS protection services for websites
Disclaimer: This content is designed to be an educational resource about VPNs and how they work, be sure to observe your local country laws and regulations to ensure your compliant.
Source(s) cited:
Michel Bakni, CC BY-SA 4.0, via Wikimedia Commons
Ludovic.ferre (talk · contribs), CC BY-SA 4.0, via Wikimedia Commons
[Online]. Available at: https://3.bp.blogspot.com/-jRNUcvAq9Nk/WS7TZi-3nmI/AAAAAAAAUyU/rnQgR7HjpdAuLuRymc1P6TVdp2o88VAzQCLcB/s1600/VPN.jpg (Accessed: 19 May 2025).
https://www.iconfinder.com/icons/4158561/download/png/512
https://www.iconfinder.com/icons/9421985/download/png/512 Via https://creativecommons.org/licenses/by/4.0/
https://www.iconfinder.com/icons/9989797/download/png/512
![logo-new-23[1] logo-new-23[1]](https://cdn-ihdfn.nitrocdn.com/eZVJvoSTyVixkEUySRKiaseNtUlmgCyu/assets/images/optimized/rev-e93b6b3/agrtech.com.au/wp-content/uploads/elementor/thumbs/logo-new-231-qad2sqbr9f0wlvza81xod18hkirbk9apc0elfhpco4.png)